Windows-based Sniffer
Contents
1. Introduction
This document is meant as a quick and dirty guide to get you up and running with Sniffer Pro. Sniffer Pro
has been developed by bringing together the Windows-based NetXRay and the original DOS-based Sniffer.
Before installing Sniffer Pro you will need to remove your network card driver, but without restarting you machine.
Do not do this unless you hava a network card that is supported by Network Associates e.g. a Xircom 10/100 Card Bus PCMCIA
card. Sniffer Pro installs its own drivers that trap error frames as well as normal traffic. With the Sniffer Pro
drivers, Expert analysis tries to decode bad frames.
Sniffer Pro has gone through many revisions and currently sits at 5.0. From
3.5 onwards the .CAP format that trace files are saved in, changes slightly so that newer .CAP files cannot be opened
by older versions of Sniffer Pro. The illustrations in this document have come from Sniffer Pro 3.5.
2. Product Description
With Sniffer Pro, you can monitor and produce statistics on a network in real time, you can perform real
time Expert analysis in real time, filter incoming frames, save captures and analyse frames in depth. You can even generate
your own traffic to simulate network conditions.
There are a number of different types of Sniffer Pro. The standalone portable analyser as software on a laptop or the custom built
Dolch type sniffers, or the Distributed Sniffer where a rack mountable Sniffer agent (Probe) is located on a site and a Distributed
Sniffer Pro Console which can access multiple remote Sniffer Probes. The Probes can have multiple NICs allowing you to connect them
to different LANs/VLANs at one time. When using switches such as Cisco Catalysts, you can connect the Probe to a port and then
'Span' that port so that it 'mirrors' other ports in the switch. Having remote access to the switch allows you to remotely
change how the Probe accesses the network with multiple segments and VLANs.
If you are on site with a Sniffer Pro and you need to examine traffic on particular port, then there are a number of ways of doing this:
- Plug into a spare port on the switch and mirror the particular port(s) that you are interested in.
This could be a Port tap, port mirroring of one device, a Switch tap, mirroring of a whole VLAN
or trunk port, or a Circuit tap which captures frames specifically from one host to another.
If you are spanning a Gigabit port on a 100BaseT port you may find that when the switch gets heavily used, you will drop
packets.
- Use a 10/100 mini hub at the user location, plug the user and the Sniffer Pro into the hub and capture
the user traffic.
- Connect to an unused 'live' floorport connection near the user, trace the patching to the port on the switch
and mirror that port.
- Attach to the patch frame directly using a modified cable using say an RJ45 socket at the end attached to the frame.
Monitoring Tools:
- Dashboard
- Host Table
- Matrix
- History Samples
- Protocol Distribution
- Global Statistics
Troubleshooting Tools:
- Alarms
- Capture Frames
- Expert Analysis
- Expert Options
- Filters
- Triggers
Decoding:
- Displaying Frames in Hex, as a summary and in detail
- Navigation
- Select Frames
- Find Frames
- Filters
- Display Setup
Managing:
- Address Book
- Packet Generator
- Ping
- Trace Route
- DNS Lookup - finds the domain name of an IP address, or finds the IP address of a domain name (Reverse Lookup)
- Finger - displays information about each logged-in user on a host.
- Who is - searches for a TCP/IP directory entry for a registered domain name, user's name or user ID.
- Scripting
You can also define your own tools using the Tools > Customise User Tools.
Sniffer Pro can be used with many different interfaces; Ethernet 10/100/1000, Token Ring 4/16, HSSI, ATM, Frame Relay etc.
3. Starting up Sniffer Pro
3.1 Running the Program
Double Click on the Sniffer Pro icon.
The first thing that you may wish to do is to filter traffic from your PC. This traffic could be browser
traffic or Netware traffic.
Each agent, or probe, has its own settings under the Sniffer Pro directory.
The title bar shows the current status of the agent being used e.g. Local Ethernet (Line Speed at 10Mbps).
With Distributed Sniffer Pro, you can switch between agents by selecting File > Settings. Otherwise
you are stuck with Local. In this dialogue box you can create new agents for different probes or if you are changing
NICs.
Below the Title bar is the Menu bar and below that is the Toolbar containing the tool icons.
The Menu bar and the Toolbar contain all the tools you need, so get to know what each one does!

On the bottom right, there are four boxes for Printing, Frames Generated, Frames Captured
and Alarms.
3.2 Distributed Sniffer
The on-site Agent or Probe, will need a port configured with a locally legitimate IP address so that there can be remote
access to it from the Distributed Sniffer software. Other 'monitor' ports are then connected into other switches. If these
switches are configurable remotely, then these ports can be configured to mirror traffic as required on a per switch basis.
Access to these remote agents can be controlled with Administrative access and User access. Users can Log in to these Agents and
peform capture, analysis etc. and the Administrator controls who has access and when, having the ability to disconnect users
if necessary.
When starting the centrally located Distributed Sniffer, you need to define each of the remote Agents with their respective
IP addresses. The user then right clicks on an agent and selects Connect as.... The user has to enter
a user name and password. The Distributed Sniffer software then runs and the user can perform monitoring analysis and traffic captures
as if the Agent was local. A user can leave Sniffer Agents running with captures etc. and log off. That user can then log on
to another Agent and perform other analyses on completely different networks. This is achieved by selecting File > Log on.
When saving a capture, the file is saved on the remote agent's hard disk. This capture can then be opened and examined from
the Distributed Sniffer even though the file is remotely located. If you want to save this file to the local hard disk
by the Distributed Sniffer, then you select File > Remote Open and choose a directory on the local hard disk. Be aware
that this may have an impact on the network links between the remote sites and the local Distributed Sniffer.
4. Monitoring
The Monitor applications are listed under the Monitor menu as well as being on the Toolbar as icons. When you start
them up they gather statistics cumulatively from when they are activated even though Monitor runs all the time that
Sniffer Pro is running. When viewing the statistics, whether
in chart, map or table format, you can choose to view them as MAC traffic, IP traffic or IPX traffic. These are
represented as tabs at the bottom left of the window.
4.1 Dashboard
The Dashboard gives you a visual depiction of the number of Packets/second, the Percentage Utilisation and
the Errors/second. You have a Gauge tab and a Detail tab. The Detail tab gives you information on the broadcasts/multicasts,
types of errors and packet size distribution. The figures are cumulative. This is very useful!
The Gauge indicates the default thresholds in red, these can be changed using Tools > Options > Thresholds.
Using the default values is recommended and you can see if traffic utilisation is hitting over 38% (Ethernet)
or 80% (Token Ring), or if Error rates are over 10%, or if broadcasts/multicasts are over 10%. These
are good guidelines!
4.2 History Samples

The History Samples allow you to gather a selection of statistics such as Packets/sec, Utilisation, Errors/sec etc.
that can be used to gain a profile or baseline of the network when it is functioning correctly. Alarm thresholds can
then be set accordingly and future trends can be spotted over time. Up to 10 of these samples can be run at any one time
and you can save them to view later in different formats and mixed in together as multiple histories. The icons on the left hand side of the
window give different display options and file export options.
You would typically look to run History Samples for up to an hour whilst looking for frame size distribution. You do
not want to have too many small frames (<256 bytes) as this is inefficient use of bandwidth.
4.3 Host Table

The Host Table displays each host that is detected on the segment/ring, along with statistics gathered for each host.
When looking at the MAC addresses
these statistics include in/out bytes/packets, broadcasts/multicasts and the various types of errors. As with all tables in
Sniffer Pro, clicking on a particular column heading sorts the data in the order of that column heading.
The IP and IPX addresses can also be displayed, the following picture is of the IP bar chart:
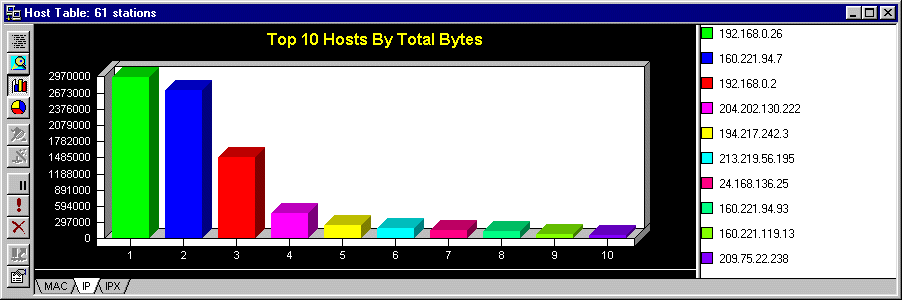
The table can be viewed in bar or pie chart format plus the statistics can be exported to a spreadsheet the format being
.csv, .txt or .prn. When viewing in Chart format, the top talkers are listed from the top on the right, and displayed
from left to right on the bar chart.
Obtaining statistics on a particular station is useful as you can filter on a station, determine the highest user, find incorrectly configured
protocol stacks, faulty NICs and export data specific to that station.
4.4 Matrix
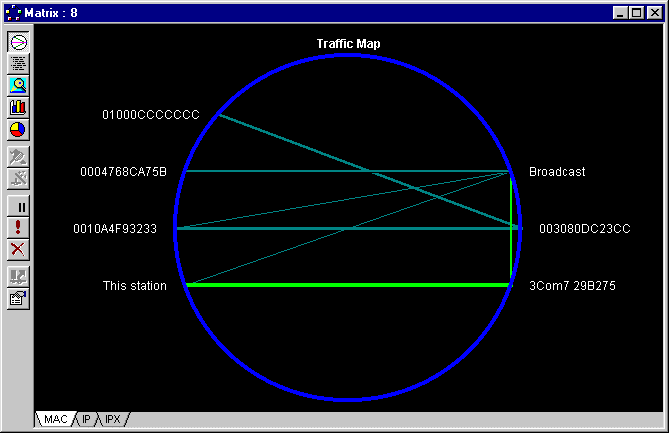
This monitoring tool gathers statistics on the traffic between stations and can be displayed as a table, a bar/pie chart
or a traffic map. You can use the Outline view to see the total activity between pairs, or separate this out
into protocols using the Detail View (magnifying glass).
The traffic map is good for a quick look at the top talkers (thickest lines) and to find who is talking to who.
Holding the mouse over a line reveals the throughput. Right-clicking allows you to zoom in and out.
The Matrix view is useful for finding devices that are not receiving or transmitting traffic and to see who is talking
to whom. You can use the tabs to view the conversations at the MAC layer or at the IP or IPX layer.
You can define filters from the Matrix View by right-clicking on a device and selecting Define Filter.
Another quick way to filter the display is to create Visual Filters. This works by clicking on the devices
that you are interested in, in the Matrix View, whilst holding down the Ctrl key. You then click
on the Visual Filter button at the top of the Matrix View window, and a new capture is created containing
just those devices.
4.5 Protocol Distribution
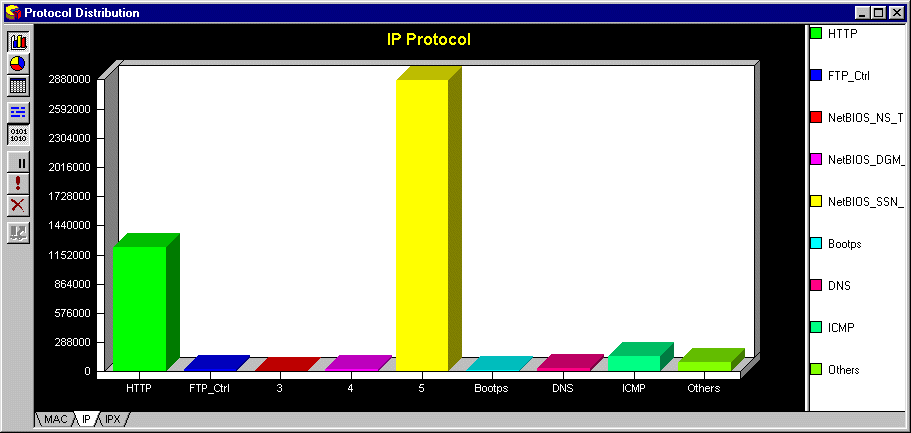
This displays the protocol distribution at layer 3 (using the MAC tab) and higher (using the IP and IPX tabs).
The example above shows the IP protocols distribution.
This can be used to find spurious protocols that should not be on the network.
Again there are different views such as Bar or Pie chart that can be used. The Table view gives a percentage distribution
of packets per protocol.
4.6 Global Statistics

This displays distribution statistics based on packet size (see above) and utilisation over the sampled time. If over the whole time
that the Global Statistics was running, the utilisation was less than 10%, then the 0%-10% column would
be at 100%.
5. Troubleshooting
5.1 Baselining
To get a feel of a network you need to have a baseline of its performance so that you can recognise
when problems have occurred. The following steps are advisable when producing a baseline:
- Take regular, say weekly, snapshots of the network at low, medium and high usage periods. These should be taken
of the VLAN backbones if possible, separate segments, links to routers, a particular user and critical devices.
- The snapshots should be for a specified time period, say 5 or 10 minutes.
- Pick the same places each time the snapshots are taken.
- Have a set of commands to measure response times by. These could include ping tests, trace routes,
SMB (Windows) file transfer, FTP file transfer etc.
- Note what the Expert system is saying.
- Save the captures and include network diagrams as part of the documentation. Sniffer Pro saves captures
in .CAP format by default. You can save files in a compressed format .CAZ if you wish. Sniffer Pro is also
able to read .ENC, .TRC and .FDC files.
- Note Relative times between client requests and server responses, this gives a baseline to test by if network
problems occur later on.
- Have a filing system that makes it easy to retrieve the data if required later.
5.2 Tools
In the Tools menu, there are tools that can help you with troubleshooting. These include Ping,
Trace Route, DNS Lookup, Finger and Whois. Select a tool and input the IP address
of the device that you are trying to reach.
6. Alarms
The Alarm Manager creates an Alarm log entry when a specified threshold is exceeded or when an Expert system
has diagnosed something. In the Dashboard, using Tools > Options > Thresholds tab you can set the High
Thresholds for each of the elements being measured. This threshold is identified graphically in the Dashboard
dial screen.
Selecting Monitor > Alarm Log, or the icon on the toolbar, displays the Alarm log. The default maximum
number of entries is 1000, however this can be increased to 99999. When the log is full, newer alrams overwrite
the oldest entries first.
To set Alarm Options use Tools > Options > Alarm tab. Here, you can enable alarms to perform an action
such as create a sound, e-mail somebody, page somebody, execute a VB script or send an SNMP trap. You do this
by clicking on Enable New Alarm and Define Actions. You can also click on Define Severity
to set one of five different levels for a particular alarm, Critical, Major, Minor, Warning
and Informational.
7. Traffic Capture
Traffic can captured into RAM or directly to a file. Once saved, this capture file (.CAP) can be recalled to look at
monitoring information, frames and Expert diagnoses.
The default buffer size is 1Mb but this can be changed to a more useful size such as 16Mb by selecting
Capture > Define Filter > Buffer tab.
You start a capture by selecting Capture > Start or by clicking on the 'Play' icon on the toolbar. Pausing and stopping
the capture is carried out the same way. When stopping the capture you can select Stop and Display to immediately view
the capture and then select File > Save as to save it, giving it a relevant name. All captures are time-stamped
so give the capture names that are relevant to the nature of the traffic/filter being examined.
You can keep an eye on the state of the Capture by selecting Capture > Capture Panel and this will tell you how much
of the buffer has been used, the number of packets captured/dropped and the buffer size.

Capture settings are defined by selecting Capture > Define Filter > Buffer tab. In here, you can set the buffer size,
whether or not to 'wrap' the capture when the buffer is full, how much of each packet to save (often you just need to see the header
rather than the whole packet, thereby saving memory) and whether or not to save the capture directly to a file.
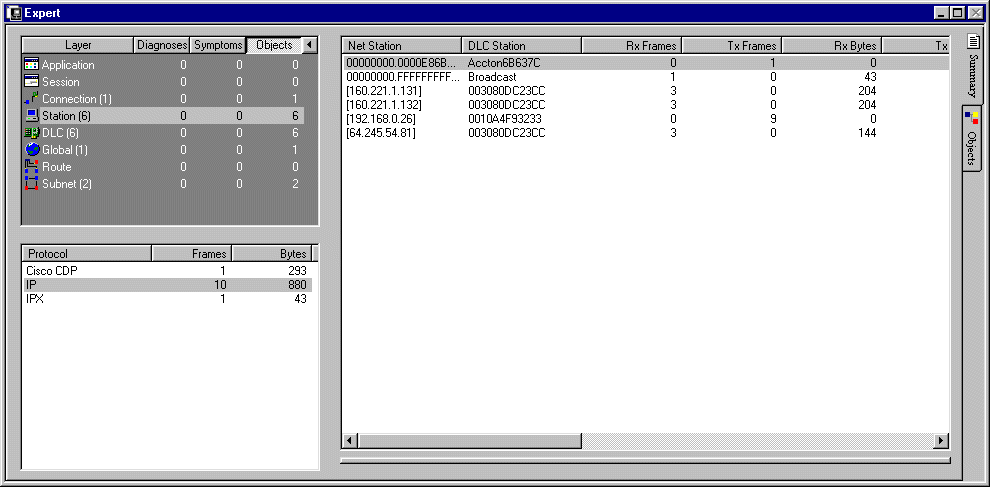
8. Expert Analysis
This system emulates human expert reasoning and knowledge to make observations on the traffic that it sees. The Expert uses
knowledge on protocols, common issues and predefined thresholds to come up with likely issues with the network. It is best to keep these
thresholds at their predefined levels as they have been calculated carefully.
Symptoms are one-off events such as exceeding a threshold. More serious are Diagnoses that indicate that a number of thresholds
have been exceeded or more fundamental network errors have been discovered.
Symptoms include events such as:
- IP frames out of order
- Maximum frame size is too short so bandwidth is being wasted
- Long ACK times
- File retransmission
- Window size exceeded
- Window Frozen
- Idle too long
Diagnoses include:
- Too many file retransmissions
- Too many Token Ring receiver congestion errors
- Duplicate network addresses
- Using a local router to reach a local node because a subnet mask is incorrect
- Broken connection
As Sniffer Pro progresses through its revisions, more and more protocols are added to Expert analysis.
The maximum number of broadcasts frames that a NIC can cope with before data frames stopped getting processed is 120 per second!
The Expert Window automatically opens when you are monitoring the network or when you are looking at a capture file.
The Expert Overview section is organised into providing comments at each of the seven network layers for each
of Diagnoses, Symptoms and the actual Objects (devices) themselves. You can expand the overview window to reorganise and
display a Summary window. You do this by clicking on the right-hand arrow at the top of the window.

When looking at Objects (as opposed to Symptoms or Diagnoses),
double-clicking an object takes you to the Object tab where you can view specific traffic, address and alarm details
for that particular object at that particular layer (e.g. Station layer, Connection layer, Session etc.).
When looking at Symptoms or Diagnoses, when you double-click on an object, you are taken to the Object window that gives you
specific symptom or diagnostic detail for that object. You can click on the ? to read an explanation and possible
causes for the symptom or diagnosis. This is very useful! The above illustration shows an explanation of a non-respsonsive station.
This window is called the Expert Explain Files and
you click on Edit > Annotate to add your own notes to a particular symptom e.g. a certain user displays this symptom when
they perform a certain action.
Older versions of Sniffer Pro only examined RIPv1 routing in the Router Expert level. If no routing protocol is detected,
Sniffer Pro automatically turns this off. To access the Router Expert options, click on Tools > Expert Options > RIP
Options tab. Here you can turn RIPv1 analysis or you can specifically monitor routing traffic from specific
routers by MAC or IP address.
Selecting the Subnet Masks tab to add masks being used on the network that are not already pre-configured on the network.
This prevents false diagnoses being made. You may for instance, be using a 23 bit mask (255.255.254.0) which is not predefined
in the list. You would then add this subnet mask.
In the Protocols tab you can define which protocols are to be examined by Expert Analysis.
In the Objects tab you define the maximum number of alarms to be monitored, which objects are to be included
in the Expert analysis and whether to run analysis during capture.
The Alarms tab allows you to define which alarms to monitor and the number of each.
9. Packet Generation
To recapture traffic from an already saved Capture file:
- Start a Capture
- Select File > Open and pick a capture file
- Select Tools > Packet Generator
- Pick the Send Current Buffer which is the rightmost icon
- You can then decide to send this capture across the network continuously, or just the once, you can stop the sending of
these frames at any time.
You can create your own frame to send out if you wish using the Send Configure button, or you
can just use the Send Current Packet button. You can also send the current packet by right-clicking
on it in the Decode Window.
Obviously you need to be careful when generating traffic across a live network. However it can be useful when diagnosing
transmission problems, testing new equipment in a lab, testing a network under load, testing NICs etc.
You can set up Sniffer Pro to be in loopback mode so that packets that are generated are not sent out on to the
network but are looped back on the interface. To configure this you select File > Loopback mode. Whilst
in Loopback mode there will be a tick visible. Interestingly, on Windows NT 4.0 there is a loopback adapter available
that you can configure as Token Ring or FDDI. This is handy if you want to examine these type of frames.
The Detail tab displays statistics such as the number of packets and bytes sent.
10. Filters
10.1 Capture Filters
Filters can be employed to minimise the amount of data being captured, monitored or displayed. Filters can also be used
to trigger traffic capture.
You can filter on source and destination addresses, errors, data patterns, particular protocols and frame sizes.
You can check that you are receiving frames with your filter by examining the Capture Panel.
10.2 Display Filters
You can also apply filters to your existing displayed capture file. To do this select Display > Select Filter
and pick a predefined filter, or create your own by selecting Display > Define Filter. Applying a filter
to an existing display automatically creates a new trace which you can save separately. Note that the frame sequence
numbers change from the original display. As you can see, there are multiple ways to access the Filter
dialogue box, via the Capture, Monitor, Display menus or via the Define Filter icon on the Toolbar.
10.3 Defining Filters

To define a filter select Capture > Define Filter. You are initially faced with the Summary tab which displays
the current filter in place. On startup, Sniffer Pro has a filter called Default that has nothing defined
such that it allow any packet of any size. You will notice, that on the far right of the toolbar a drop-down box exists
with the name default in it. As you build your different filters, they can be selected from this drop-down box
and used.
Rather than modify the Default filter, select Profiles then click on New, enter a new profile name and
select Copy Existing Profile or select a Sample Profile from a large list of predefined filters
for different protocols. Eventually, you can build up your own set of filters to suit the environment and projects
that you are involved with.
The Summary tab displays the overview of the whole filter with all its aspects.

The Address tab is used to define a filter between devices based on MAC layer or protocol layer addresses.
You can specify paricular conversation pairs, or one to all or all to one. You can select the Include mode or
the Exclude mode depending on your requirements for the filter. Up to 10 address pairs can be specified.
You can store oft-used addresses in an Address Book and you can access this address book from this
Address tab.

Using the Advanced tab allows you to filter based not just on addresses but also on protocol type e.g. ICMP, IGRP,
Appletalk etc. You can also filter on packet size or type e.g. CRC errors, Jabbers etc. This is useful when triggering captures.
As well as using addresses to filter frames you can use the Data Pattern tab to filter based on patterns.
Multiple patterns can be included/excluded dependent on the boolean operators AND, OR or NOT that are selected.
This way of filtering is used particularly when filtering already captured frames and we can select existing patterns.
The pattern sequence can be anything up to 32 bytes in length and its starting point is defined by the Offset
(see later in the description of Hex View). This offset can be defined as being from the beginning of the packet, or
the protocol, as defined in the From field. The protocol meaning the layer 3 protocol such as the IP
or IPX header.

To set up a Data pattern right-click on a frame from the Summary View and select Define Filter.
Select the Data Pattern tab. Start by picking Add Pattern and you are presented with
the frame in the lower window, its frame number is displayed on the right.

You can click in this frame display to the protocol header that you want, or the
Session layer information e.g. ( in a telnet session. When you pick this part of the frame
and click on Set Data, the offset is automatically
calculated, and the hex byte for that character is added in the first location on the pattern.
The pattern length depends on what you pick, for instance if you pick a MAC address, the pattern length
is 6 bytes. This pattern copy and paste is much easier than trying to calculate the pattern that you want
and then manually working out the offset, although sometimes this will be your only option if you do not
have a capture of a frame with an example pattern.
You can select binary patterns instead of hex if you wish. The offset and length fields change accordingly.
The Boolean AND operation means that all patterns that are ANDed together must be present in the frame
for it to pass. Using the Boolean OR means that anyone of the patterns needs to present. Using
the Boolean NOT excludes frames from the display that match the pattern. The Evaluate button
gives you an indication of whether your filter will work, it returns nothing if the filter will work.
10.4 Triggers
Triggers can be used to start a capture or stop and save a capture. This is ideal for grabbing the moment when those spurious
hard to find network issues.

To set up a trigger select Capture > Trigger Setup. You can decide to start a capture based on a defined filter
e.g. packets with FTP control of a particular user. You may then want to stop the capture when you see the user password.
The filter for this would search for a hex pattern with the username and password. Clicking on the Repeat Mode button
would allow you to repeat this if you wished, otherwise these triggers would just run the capture once.
You can also trigger depending on an alarm or the time.
11. Decoding Traces
You can only analyse the packets of a saved trace, you cannot analyse packet detail when capturing or monitoring.
Upon opening a capture file you select the Decode tab and you are presented with three main windows, a
Summary View, a Detail View and a Hex View.
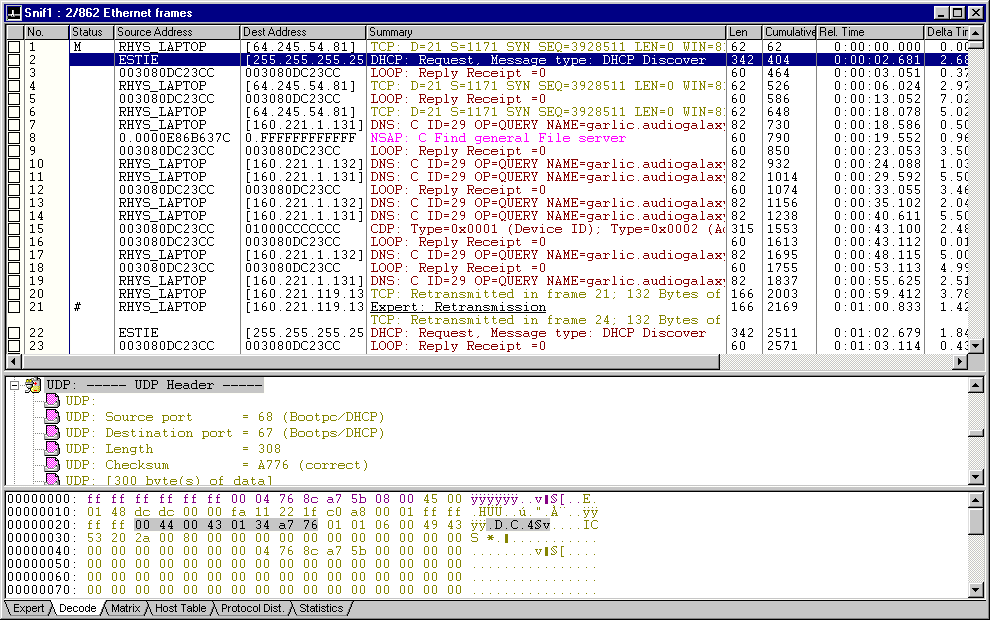
11.1 Summary View
The summary view displays the most important information on the captured packets. The following lists the column number
and their meaning:
- This is used for ticking frames for later access and saving separately as separate captures of interest.
- This displays the frame number in that particular capture.
- This displays the status of the frame using the following key:
- # - a Symptom or Diagnoses is associated with this frame
- Trigger - this frame is an event filter trigger
- CRC - normal packet size with CRC error
- Jabber - oversize packet with CRC error
- Runt - undersize packet with valid CRC
- Fragment - undersize packet with invalid CRC
- Oversize - packet larger than 1518 bytes, with a valid CRC
- Collision - packet damaged by collision
- Alignment - packet length is not a multiple of 8
- Dup Address - Token Ring address conflict
- Frame Copy - Packet not copied by destination
- M - Marked frame. To mark a frame, right click on it and select Mark Frame.
- The Source address
- The Destination address
- The Summary describing the type of packet
- The packet length excluding the CRC, i.e. a 64 byte frame shows as 60 bytes here.
- The Relative time from when the packet arrived starting at the marked frame (default 0 for the first packet in the capture).
You can mark a frame say from a client and see the relative time build up in the conversation with a server.
- The Delta time i.e. time between this frame and the previous one. You can use this to see how quickly
a server is responding to a client. The format of delta time is seconds.000.000
- Absolute time
- Cumulative Bytes can be used to measure the number of bytes that a particular conversation takes. The Frame Length bytes
are counted up from the marked frame (this column is not displayed by default). The efficiency of a given protocol
can be calculated by the formula Overhead = Cumulative bytes - User Data. The volume of User data would be found
by looking at the data/file sizes being transferred.
By default, the addresses displayed are Layer 3 addresses, if you want to look at devices by MAC address, then
select Display > Display Setup > Summary Display tab and click off the Show Network Address option.
You will notice that this Display Setup box gives you fine control on the display of the Decoded trace. You can
display by host to host conversation, decide which columns are included, change the colours of the protocol layers,
change the dispaly fonts
and whether or not to show all layers in the Summary View (useful if you do not want to keep dipping into the Detail
View.
When looking at a summary of the conversation side by side by selecting Display > Display Setup > Summary Display tab
and clicking on Two-station format, you can then see how the conversation pans out frame by frame and look at delays between frames etc.
It is useful to create a filter that just looks at the two hosts.
Pressing F8 takes you on to the next frame in the Summary View whilst pressing F7 takes you one frame backwards at a time.
11.2 Detail and Hex Views
The Detail view displays the detail for each protocol header in each frame. The software tells you what each byte and even
each bit acting as a flag means. Each layer has a different colour, by default the Data Link Control (DLC Layer 2) is
coloured purple, TCP/IP (layer 3/4) is coloured pea-green and the Session Layer 5 is pink. These colours can be changed
in the Display Setup.
The Hex View displays the hex values of the binary stream. On the left hand side you have the offset values in hexadecimal,
then in the middle you have 16 bytes (in 4-bit pairs) of hexadecimal which is the frame itself, followed on the right by the
ASCII equivalent of those 16 bytes (this can be changed to EBCDIC if you wished). The frame is laid out on a row by row basis.
The offset values indicate where each row starts on a per frame basis. You will notice that the first offset value for a
particular frame is 00000000 thereby indicating the start of the frame. The next offset value is 00000010
and indicates that the first hexadecimal character of this next row is 0x10 bytes (1610) into the frame.
The offset values in the Hex view are useful for when you are setting filters using pattern matching for certain parts
of the frame header. For instance if the starting offset for a row is 00000010, then the bytes located
at offset 0000001E are found by counting along 15 bytes (remember the first pair on the row is at offset
00000010!).
When you highlight any part of the Detail view, the corresponding part of the frame is highlighted in the Hex View.
The converse is also true.
11.3 Navigation
Use the following keys to move around the Decode views:
- Tab to move between views
- F8 moves on a frame
- F7 moves back a frame
- F4 zooms on to one view only, and back again to the three views
- Home takes you to the top of the particular view that you are in
- End takes you to the bottom of the particular view that you are in
- F2 moves you on to the next 'selected frame' i.e. the frames that are checked in the first column of the summary view.
- shift+F2 moves you back to the previously checked frame.
Right-clicking on any of the windows gives you access to options such as moving to frames, defining filters, changing
from ASCII to EBCDIC etc.
To find particular frames use Display > Find Frame or press Alt + F3. To find particular
addresses select the Detail text option. You use the Detail text option when looking for data or text.
By selecting the Data tab you can search for data patterns just as you would when creating a filter.
The Expert tab lists the various Symptoms and Diagnoses that occur in the trace and you can search
for frames that match one of these.
Using Display > Go To Frame allows you to go straight to a frame number (left-hand column in the Summary View).
You can select individual frames by clicking on the boxes in the Summary View, or you can select a range of frames
using Display > Select Range and by entering a start and finish number. The selected frames can be saved
as a separate trace by right-clicking the mouse and picking Save Selected.
12. Management
Back to the top
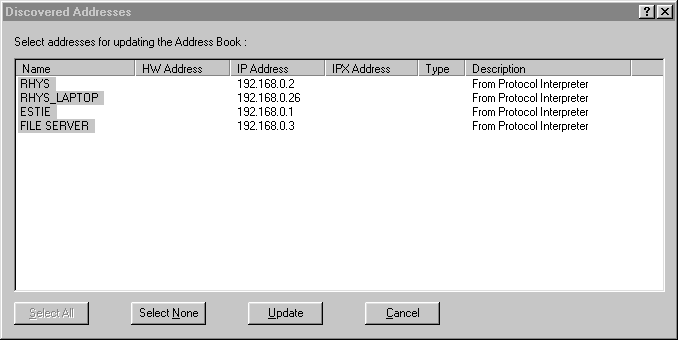
If you have a trace open and you select Display > Discovered Addresses, you will see a list of names and
addresses that the Sniffer has learned from the protocols. You can select some or all of these and Update
them to the Address Book. Once updated, you can retrieve the Address Book by selecting Tools > Address Book.
In the Address Book, you can add new addresses manually, edit existing addresses, delete them and export them to a CSV
file. You can also set up the address book to either actively search for IP addresses by selecting a range, or
passively search for addresses as they appear on the network.
You save the Address Book by selecting Database > Save Address Book.
Sometimes you can get a protocol that is encapsulated within another protocol e.g IPX in IP, or the frames are damaged.
To do this select Tools > Options > Protocol Forcing and pick the protocol that you wish to be forced. You will need
to set the number of bytes to skip in order to get to the start of the forced protocol.
In the Program directory there are some Visual Basic script files (.BAS) that can be used to automatically activate
the Sniffer when an alarm sounds (ALARM.BAS), export trend data, send an SNMP trap (XRAYALRM.BAS),
import address data etc. Plus you can write your own scripts. Scripts are run by selecting File > Run Script.
You can , if you wish, have multiple agents configured on one adapter by selecting File > Select Settings > New
and then using the same network adapter and Copy Settings from field.
Each session that you run can examine a different aspect of the traffic. The number of simultaneous sessions will
depend on your CPU.

|

